Kick the bucket
I already wrote a post about Amazon S3 buckets but they became so popular these last weeks that many people explain what is a bucket, what is the danger and how to exploit misconfiguration. My goal here is more: how/where to find those vulnerable buckets.
First I assume you already know the basics, if not, you can read the excellent article from Frans Rosen on Detectify.
How a bucket name looks like?
After analyzing alot of buckets, here are the most common pattern I found:
- <main_name><separator><word>
- <word><separator><main_name>
- <subdomain>
Where main_name usually is the name of the company or the domain and separator usually is a dot . or a dash -, example:
- 10degres-static
- prod.10degres
- assets.10degres.net
It’s also very common to find multiple “level” of separation, example:
- 10degres-backups-2016
- dev.www.10degres.net
Pretty rare, but sometimes separators are mixed:
- img-dev.10degres.net
- static.10-degres.net
How to access a bucket?
There is 4 ways to access a bucket:
- subdomain of s3.amazonaws.com, ex:
https://xxxxxxxxxx.s3.amazonaws.com - subdirectory of s3.amazonaws.com, ex:
https://s3.amazonaws.com/xxxxxxxxxx - subdomain of Cloudfront, ex:
https://xxxxxxxxxx.cloudfront.net awsclithe command line environment tool for AWS, ex:aws s3 ls s3://xxxxxxxxxx
From here you probably already guessed the next chapter…
How to find buckets?
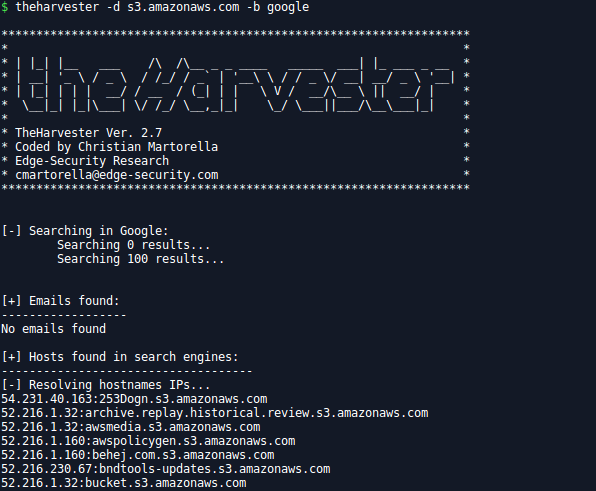
To Find buckets, you can use the tools you already use when you perform recon on a new program/domain/host:
-
sudbomain discovery: Sublist3r, dnsrecon, altdns, threadcrowd.org…
-
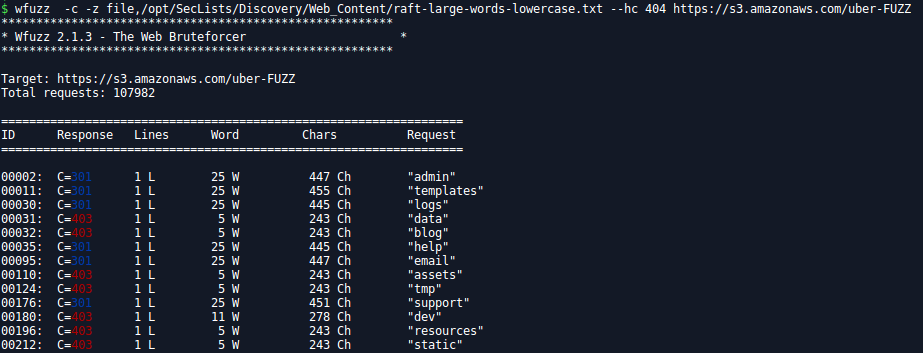
subdirectory discovery: dirb, wfuzz, gobuster…
-
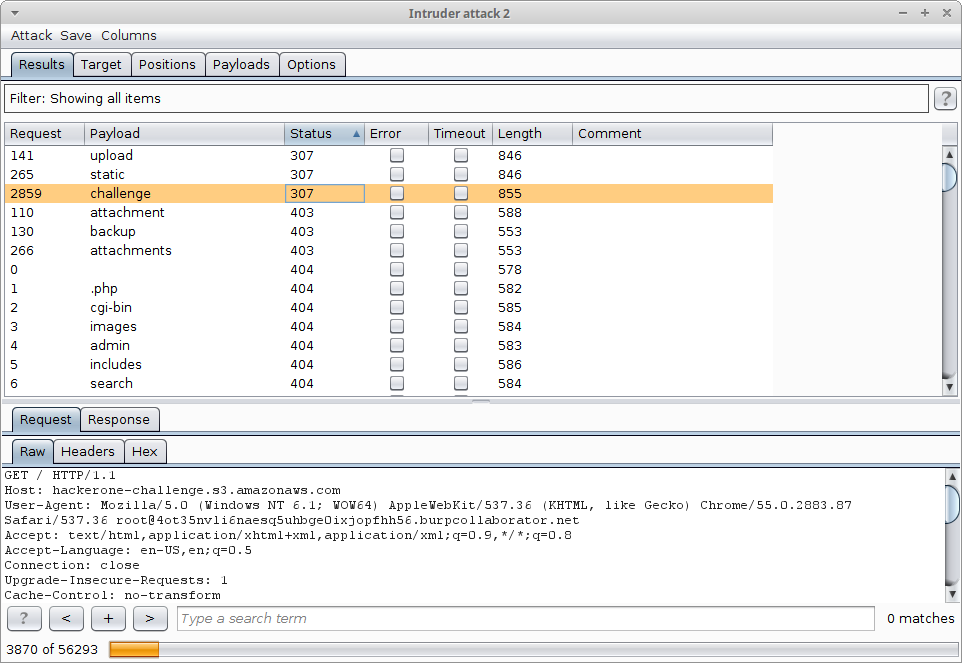
both: Google, Burp Suite and many others…
Dedicated tools
Some dedicated tools have been released to discover buckets:
- Bucket Finder by DigiNinja
- laszyS3 by Jobert Abma and Ben Sadeghipour
- bucketlist by Michen Riksen
- s3-bucket-finder by me
I also wrote a small script that try to determine what is behind a Cloudfront subdomain.
Additionnal notes
Even if a bucket is read only, you can report it if the datas available are hot, take a look at Hackerone where the researcher wrote a report to Mapbox and got a nice reward.
Even if a bucket is empty, you can also report it, the danger still here, a hacker could use the place to store hacked datas (movies, software…) or serve malicious files.
A bucket can be readable from the command line tool awscli but not with your browser, try both way.
All files contained in a bucket can have different permissions, test them all.
A bucket can be configured to serve only one region, you will get a very specific message in that case, so test all region to find the good one (see the region list).
Some buckets are not reachable via http, you should prefer https.
At this time, there is no real way to know the owner of a bucket. The only thing you can do, if you have access to the ACL (via the command line method get-bucket-acl), is to compare the owner of two different buckets. So take care when/who you send a report.







