One takeover to rule them all
Because of Covid, the first quarantaine in France occured in March 2020. During that time I wrote a Python script to detect Subdomain Takeover. As I have been successful several times with the tool, one hit was especially beautiful.
The story of how I have been able to take control of 450+ subdomains of the national french electricity company EDF.
I'm not going to explain what is subdomain takeover so take a look at the following articles if you want to know more:
OWASP test guide
Hackerone guide
0xpatrik basics
As we all know there are several ways to takeover a subdomain but the easiest way is probably to buy an expired domain which is available for purchase.
Using my tool dnspy, I found that
nucleaire.edf.fr was an alias of edf-linkbynet.com.
A quick search on Gandi and I realized that last one was available for purchase for about 12€/year.
Not knowing what would happen next, I bought the domain and configured it on my server to serve a nice PoC page.
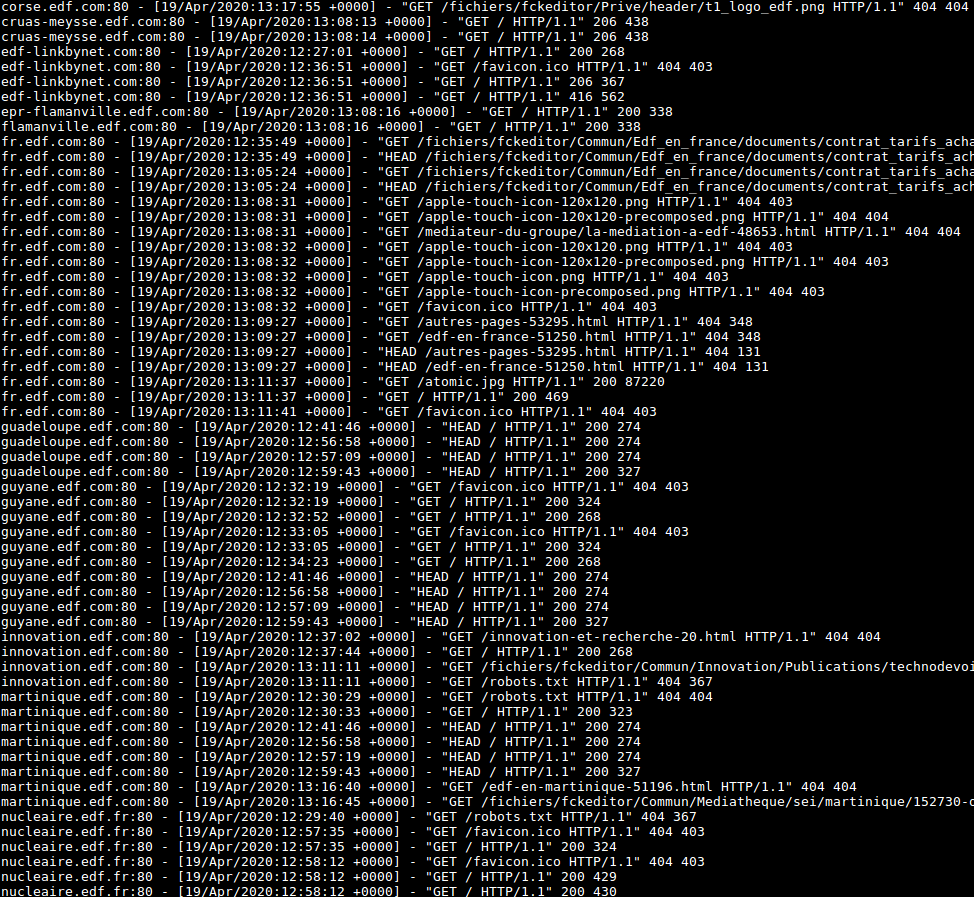
A few days later, I checked my server logs to see if anyone requested the stolen subdomain. What was my surprise when I noticed all those requests for different subdomains I didn't know anything about.
At that time EDF had a private bug bounty program on the french platform YesWeHack.
I was not invited so I used the dedicated contact form on their website.
6 weeks later and several tries to get in touch with them, the problem was magically and silently fixed.
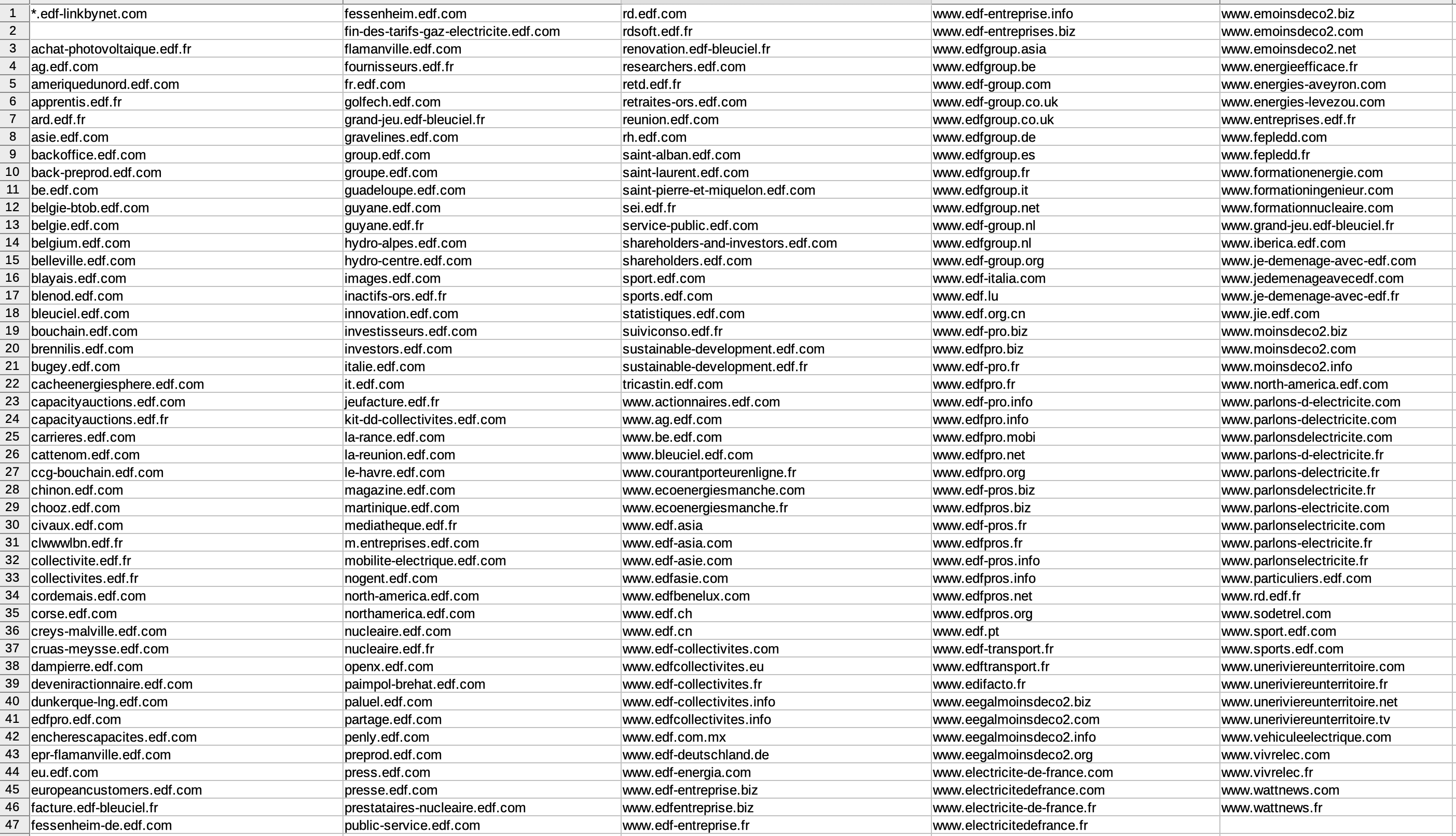
At the end more than 450 subdomains were redirected to my server. Exploited by a malicious user, it could have been devastating: social engineering, phishing, cookies manipulation, fake payment system, company reputation… (a simple “thank you” would have been appreciated).
Regardind the issue itself, my guess is a bad communication between tech team leaders.
One admin bought edf-linkbynet.FR and the other one configured all CNAMEs to point to edf-linkbynet.COM, as simple as that!
The tool
The tool, called dnspy, is composed of 3 modules:
1/ the grabber tries to find subdomains using external tools like subfinder, oneforall, github, amass… then alterations are created using altdns or dnsgen.
2/ the resolver performs DNS queries on all subdomains grabbed and generated using massdns, trying to detect dead hosts, cnames…
3/ the interpreter reads the output of the resolver and looks for possible takeover using the fingerprint file. It’s inspired of subjack with some extra features like regexps support and an ignore list.
The whole thing is daemon based and can be independently launched. Below some good findings.